
Home

All Speed Tips

Other Tips

Optimization Software

Tech News

Internet Security

Ask The PC Expert

Computer Jargon

Contact Us

Subscribe via Email

Subscribe via RSS



Recent Articles
Learn To Repair PCs With The Right Course
Buying a Refurbished PC
How to Optimize Droid Razr Battery
|
|
How to use a Firewall effectively
A small introduction to the firewall
The Firewall is a special feature added to the Windows XP Service pack 2 which was formerly known as Internet Connection Firewall or ICF. Theoretically, it acts as boundary between your computer and the outer world. You can call it a watchdog for your Windows. It sits and waits for any attack on your system. Now this is not the way in which Microsoft would like to describe this feature. In a technical language, as said by guys at Microsoft, "stateful host firewall that drops all unsolicited incoming traffic that does not correspond to either traffic sent in response to a request of the computer (solicited traffic) or unsolicited traffic that has been specified as allowed (excepted traffic)". This is not so easy to understand!
In a nutshell, when any application installed on your system tries to make contact with the outer world, say on your work network or Internet, it has to go through the firewall and the firewall will report it to you. Moreover, if anyone else or any application from the outer web space tries to make contact with your PC, then it will also get blocked by the firewall.
First of all, when you install Windows on your machine, the Firewall is turned "On" by default. All incoming and outgoing traffic is being monitored by your firewall in this situation.
If there is any unsolicited traffic in or from your PC, the windows firewall will notify you. When it does notify you of a program making unsolicited contact and you identify the program as a valid one, you will then need to add an exception to your Firewall's configuration.
Even though firewall identifies some programs as malicious ones, they are not. You will have to be careful deciding that.
Let's have a look on my exception list. To do it yourself, go to "Start -> Control Panel -> Security Center" and the following window will pop up.
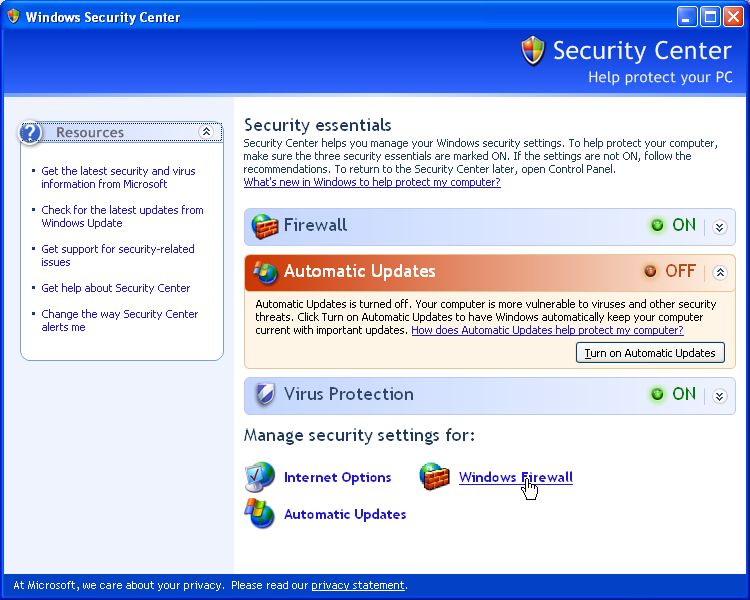
Now click on the "Windows Firewall" Option and the following window will open.
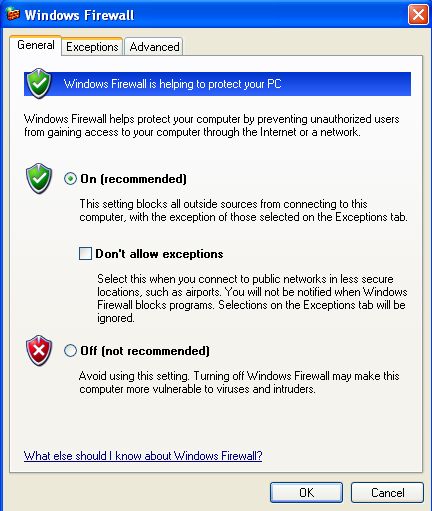
In the Top menu, you can see the option for, "Exception". Click on that.
In the next screen you can see a long list containing various applications' names. Let's take the example of "uTorren". As we all know it's a Torrent client. So it needs to connect to outer network both on my home network and to the Internet. It downloads various files when I ask it to do so. But when I first installed the application, the firewall identified it as a threat to my PC and blocked it. However, after I added it as an "Exception", everything is fine. The incoming traffic concept is well explained by this example.
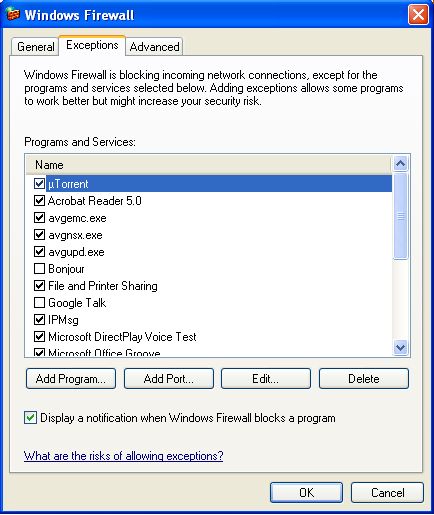
But what about outgoing traffic? To make it simpler, let's take an example of an Internet messenger like GTalk. When you are in a conversion with your buddy, you encounter both incoming and outgoing traffic which is also monitored by the firewall. So to make it possible, you will need to let your firewall know beforehand.
Sometimes the firewall does it automatically for you and when it doesn't you can do it yourself. In the same window above, you can see an option for "Add Program", click on that. And you will be presented with the list of all programs installed on your system and you can select one from that list.
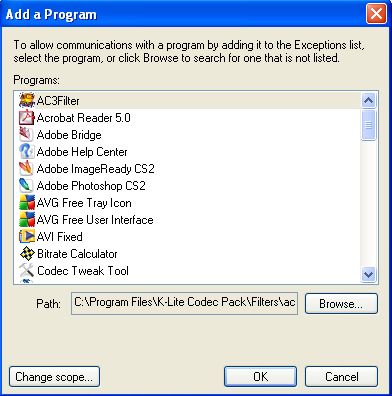
Just click on the "Ok" button after selecting the program.
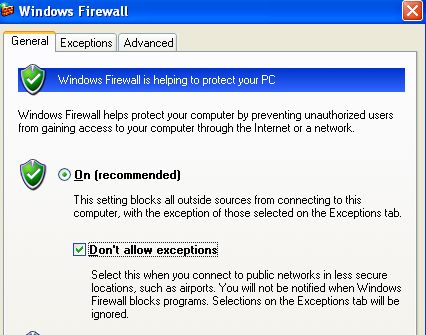
Sometimes when we work on a network where tight security is required, we simply don't need to add any exception to the list. In that scenario, you can select the "Don't allow exceptions" option as shown below.
Also, if you are somewhat an advanced user then click on the "Advanced" tab on the Top menu. The following window will open up,
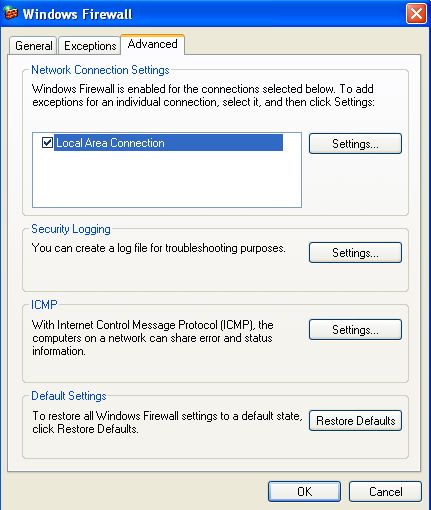
You can see many options there: "Network Connection Settings", "Security Logging", "ICMP", and "Default Settings".
Under "Network Connection Settings" you can select which network connection you want to monitor using the firewall or not in case when you have various kinds of networks like LAN, Wireless etc. You can even select various services through the "Settings..." tab.
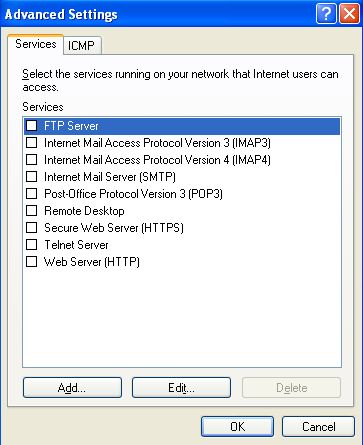
Options to select from are FTP server, Telnet, IMAP, HTTP, HTTPS etc. You should know what you are doing before you make any changes here.
You can also make it so the firewall logs a report when it does something to your system. To enable it, select the "Settings..." tab in the "Security Logging" area. The following window will open up,
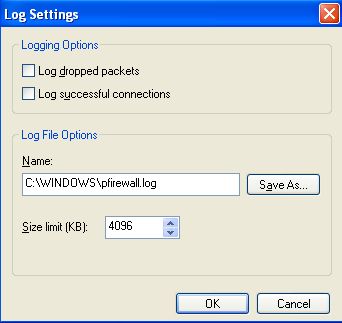
Just toggle the option you want to turn on or off and each option is self explanatory.
Another one which shouldn't be left out is "ICMP" or Internet Control Message Protocol. As the name suggests it totally controls how your PC makes contact over the Internet. When you click on the "Settings..." tab the following window will pop up,
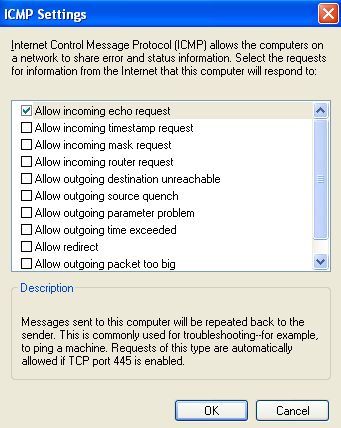
The first option you see is "Allow incoming echo request". Well by default it's necessary to do so. By "echo"ing a machine you can identify whether a PC is live or not. Just for an example, take our website http://www.computertooslow.com/ and it is live as you are reading this article. See the result of the following command on my PC,
Ping www.computertooslow.com
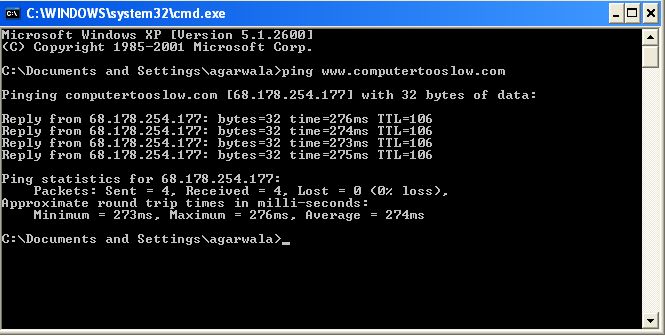
So the PC on the server side responds well to this command only because this option is checked on this list.
So, now that you know all about your Firewall, you can engage in safe web surfing. Don't forget, a firewall only protects you against worms which spread through the network, not against viruses or spyware!
If you enjoyed this post, please
or
|
-By Dominic
Web site and all contents © Copyright ComputerTooSlow.com 2012, All rights reserved.
|
|